RedTail, Remnux and Malware Management [Guest Diary]
[This is a Guest Diary by Jacob Claycamp, an ISC intern as part of the SANS.edu BACS program]
Introduction
When I first saw malware being uploaded to my honeypot, I was lacking the requisite experience to reverse engineer it, and to understand what was happening with the code. Even though I could use any text editor to examine the associated scripts that were being uploaded with RedTail malware, I couldn’t see what was happening with the redtail malware itself. So, I decided to create a how-to on setting up a malware analysis program.
The malware analysis platform I chose to use, is Remnux which is a linux distribution, packaged with a variety of analysis tools originally created by Lenny Zeltser, a SANS instructor. [1] [2] My original intent for the Remnux environment was to set it up inside a docker, so it was completely isolated from my computer. This way if I accidently detonated a malware sample, I could easily just wipe away the docker. I can also wipe away the docker, after I’ve finished analyzing a sample, and start with a fresh install each time I begin a new investigation.
For this how-to, I’ll also make use of kasm workspaces which is a docker container streaming platform, and I’ll deploy it inside of a free tier of AWS EC2 instance, this approach will make it easy to access your workspace, from a web browser.
Setup
1. First you need to launch an EC2 instance in AWS. Go to the AWS Sign Up page. You can follow this website for initial account setup: [3] Sign Up For An AWS Account. I won’t go to deep into setting up an EC2 instance as you can follow along with the linked GitHub page above. However, for the Kasm Workspaces setup, you’ll need to create an EC2 instance with 2 vcpu’s, 16 gigs of ram, and 100GB disc, which is the minimum needed for a Kasm Remnux workspace install. Also, be sure to allow http and https traffic inbound. The rest of the setup above, should be followed exactly.
2. Once you’ve deployed an ubuntu 20.04 with the RSA key, log into your EC2 instance with: ssh -I rsatoken.pem ubuntu@<whatever your IP is
3. Then to install the kasm workspace perform these commands:
cd /tmp
curl -O https://kasm-static-content.s3.amazonaws.com/kasm_release_1.16.1.98d6fa.tar.gz tar -xf kasm_release_1.16.1.98d6fa.tar.gz
sudo bash kasm_release/install.sh
4. You’ll be asked if you want to create a swap partition, click “Yes” and the 8GB swap size is fine. It’ll take about 5 minutes to finish installing so be patient.
5. When it finishes, it’ll output the credentials you’ll need to access it. Copy these off and store them somewhere securely.
6. Once you’ve finished installing, return to your web browser, and enter in https://<ip of your EC2 instance> and login with the admin@kasm.local credential.
7. Once you’ve logged in, click the workspaces link on the left side of the screen and you’ll be presented with the below option. Kasm comes complete with a large variety of workspaces you can chose from. Select “Add from Registry” as seen in the screen shot below.
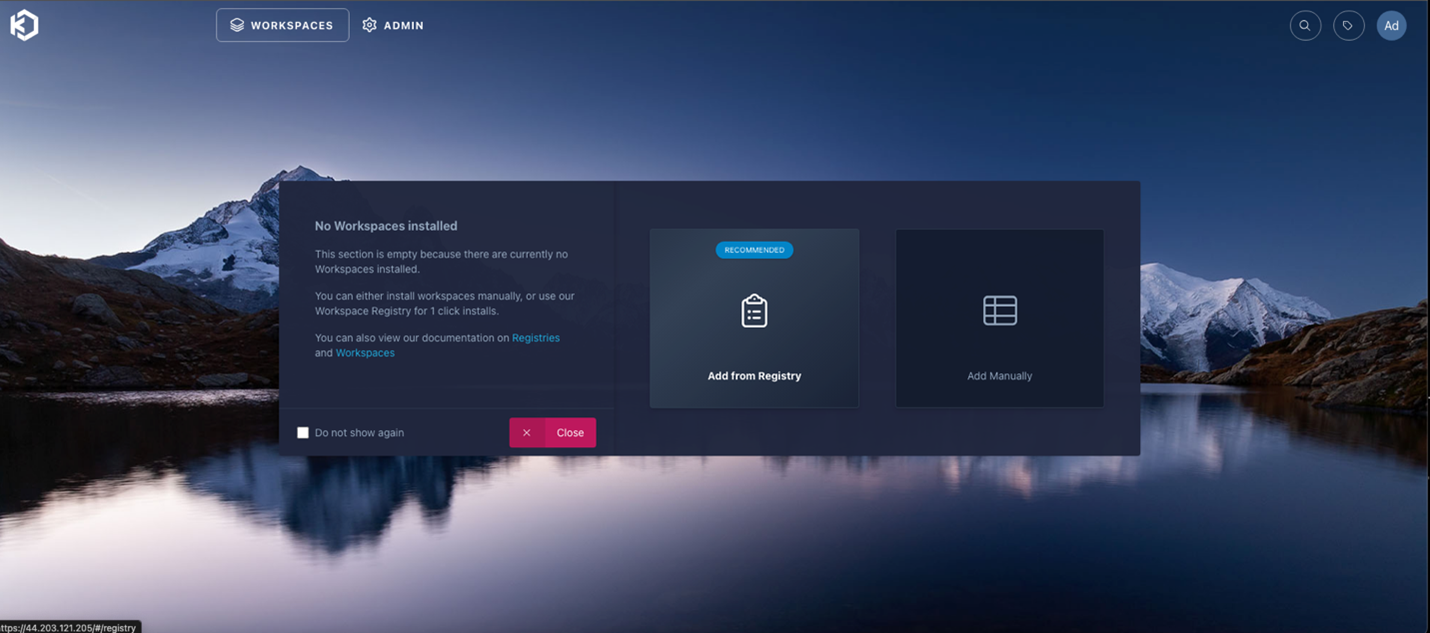
8. Once that is complete, you can search for Remnux and select “install”. It will take about 10-15 minutes to install. When it’s finished it should be present in your “Workspaces” tab, in the admin control center. Ensure the “enabled” switch is toggled on.
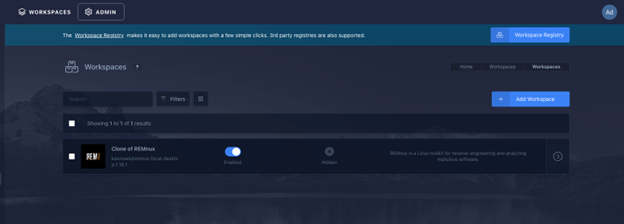
9. Next, click the workspaces link to the left of the Admin button at the top of the page.

10. Now you’re ready to go. Click the Remnux Desktop in the middle of the screen. It will launch a Remnux virtual machine, right in your web browser.

11. Time to analyze the RedTail malware. First, we need to upload a sample to our Remnux. Click the tab to the left of the Downloads and Uploads folder, and then click on upload. Once you’ve uploaded your file to the machine, it’ll appear in the “uploads folder”
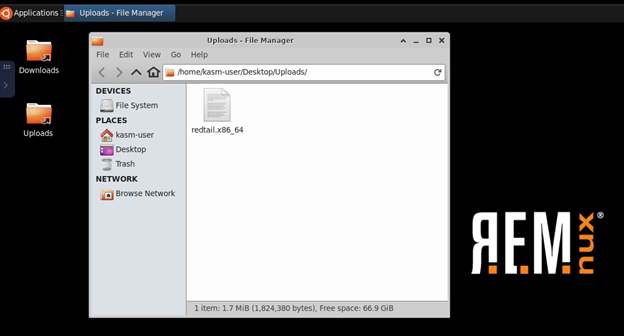
When it comes to analyzing malware, there’s 2 different approaches that should both be used. Analyze the malware statically first, that is, with the program at rest on your disc drive. We first need to identify what type of file it is. In a terminal on your Remnux box, we’ll use the file command to identify it.
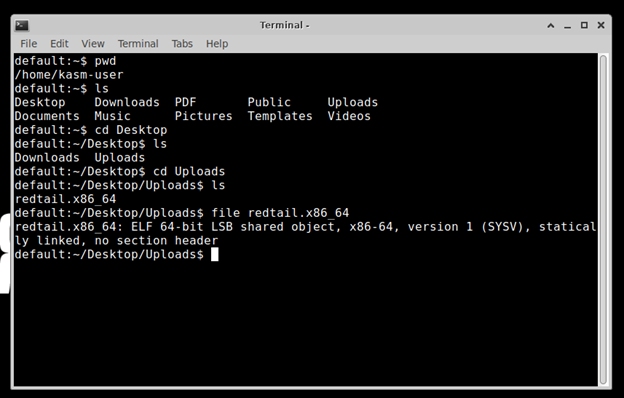
We can see it’s an ELF 64-bit file based on x86 CPU architecture. An ELF file, which stands for Executable and Linkable Format, is a standard file format used for storing executable programs, libraries, and object files on operating systems like Linux and macOS. The next static analysis utility we can use is called Detect It Easy (die) just by typing die into the command line. This program will tell us what operating system it was compiled on, what compiler was used and what programming language. However, for our RedTail sample, it’s clearly been packed with UPX, so we can’t immediately discern what the language for this is.
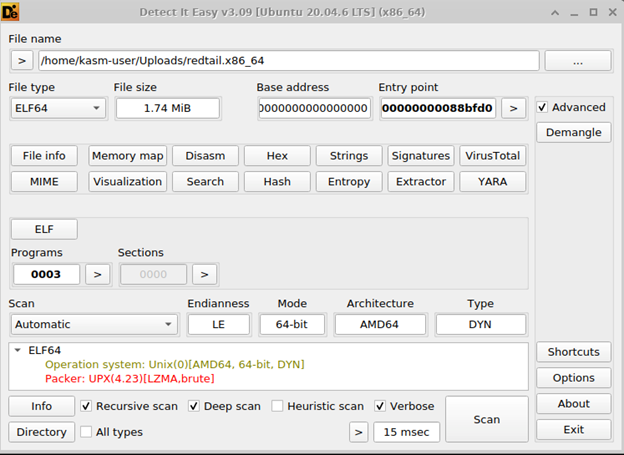
In the context of UPX (Ultimate Packer for eXecutables), the ‘LZMA, brute’ flags indicates that it was packed with the LZMA compression algorithm, and the ‘brute’ is a command line option that forces UPX to try all available compression methods, to find the best compression ratio. We’ll need to unpack it first. I actually needed to download a newer version of UPX, because the Remnux upx packer was out of date. But once that was done I just ran ./upx -d <file>
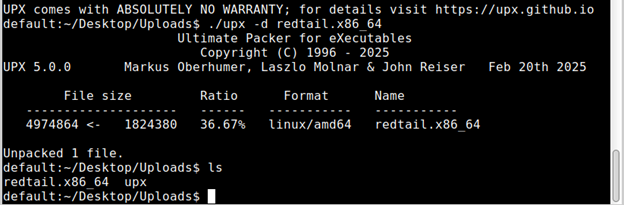
Now we can go back to our Detect It Easy (die) application and see if we’ve successfully unpacked it.
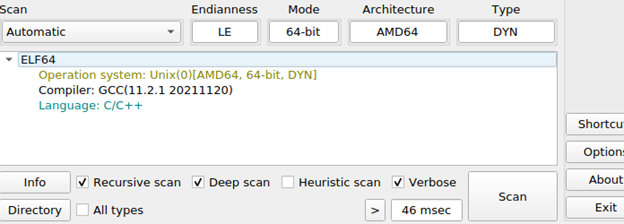
We know now it was compiled using GCC, in C/C++. The next thing we could do is run the strings command on the sample, now that it’s unpacked to see if there’s any additional base64 encoded commands, or other interesting plain text ASCII strings in there. I won’t provide a screen shot of the strings command for this RedTail sample, as they’re too numerous to display.
Finally, we’ll examine this sample with [4] Ghidra. Ghidra is a very popular malware analysis tool, developed by the NSA which can be used to decompile a binary file, read its source code, and debug it while performing dynamic analysis. You’ll find the Ghidra application under the Applications tab at the top left, and then under the Dev folder. When Ghidra first launches, you’ll need to create a new project first before you can do any dynamic analysis. For my project I just called it Redtail.
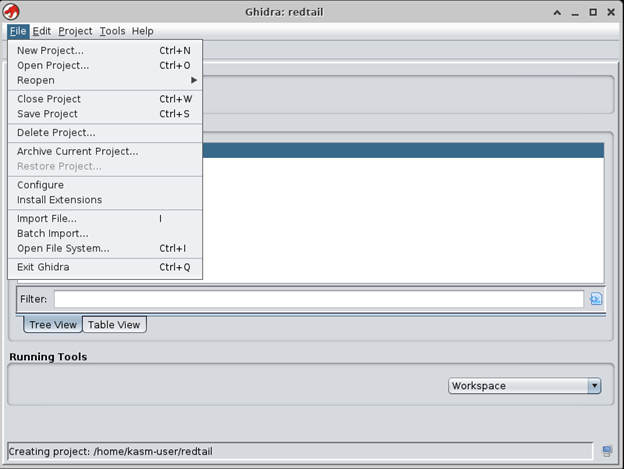
Next, you’ll need to import the malware sample. Select “Import File…” Once it’s imported it’ll give you a lot of information such as the address size, processor architecture, file hashes, etc. You can close the “import summary” file and then you’ll see your project folder with your imported file. Double-click the sample and continue with the “analyze” button.
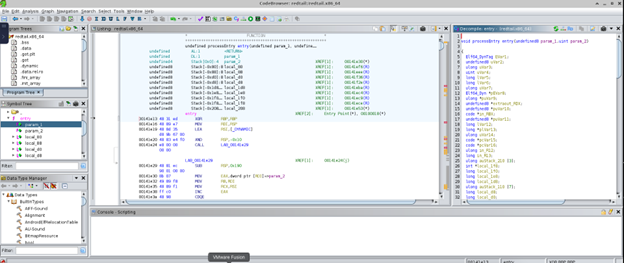
Under the Symbol Tree pane, there should be a main function or an entry function which is where the main program is written. As you can see from the screenshot above, RedTail malware is complex, with many functions referenced in the entry, and because of this complexity, I won’t dive into it any further.
Conclusion
The above is a how-to on setting up a dockerized cloud instance for malware analysis, which provides for containment, as well as easy reset to baseline. Then I provide some very basic entry level analysis techniques. Even if you aren’t good at programming or reading program language, the techniques in this article are still very useful in pulling out IOC’s, file hashes, etc, and comparing samples. Many threat actors will take a particular sample of malware and modify it to accomplish something slightly different. Not all malware is as complex as Redtail. Some malware is only a few lines of code, and you can quickly understand what it’s doing. With Ghidra you can track a malwares’ evolution over time and determine how it’s being modified and employed. If you wish to get further into the forest of malware, I encourage you to check out Lenny Zeltser’s webpage, [5] and if you want an even deeper lesson into malware analysis, check out his presentation to the RSA Conference in 2021. [6]
[1] https://remnux.org/
[2] https://www.sans.org/profiles/lenny-zeltser/
[3] https://github.com/15HzMonitor/Internship-Blog-Post/blob/main/1.%20AWS%20DShield%20Sensor%20Setup.md#sign-up-for-an-aws-account
[4] https://ghidra-sre.org/
[5] zeltser.com
[6] https://zeltser.com/media/docs/malware-analysis-remnux.pdf
[7] https://www.sans.edu/cyber-security-programs/bachelors-degree/
-----------
Guy Bruneau IPSS Inc.
My GitHub Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
Apple Patches Exploited Vulnerability
Today, Apple patched two vulnerabilities that had already been exploited. The vulnerabilities were exploited against iOS but also exist in macOS, tvOS, and visionOS. Apple released updates for all affected operating systems.
| iOS 18.4.1 and iPadOS 18.4.1 | macOS Sequoia 15.4.1 | tvOS 18.4.1 | visionOS 2.4.1 |
|---|---|---|---|
| CVE-2025-31200: Processing an audio stream in a maliciously crafted media file may result in code execution. Apple is aware of a report that this issue may have been exploited in an extremely sophisticated attack against specific targeted individuals on iOS.. Affects CoreAudio |
|||
| x | x | x | x |
| CVE-2025-31201: An attacker with arbitrary read and write capability may be able to bypass Pointer Authentication. Apple is aware of a report that this issue may have been exploited in an extremely sophisticated attack against specific targeted individuals on iOS.. Affects RPAC |
|||
| x | x | x | x |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|


Comments